
In today's world, cybersecurity actions in critical spaces have become increasingly commonplace, with dedicated teams directly protecting the assets, reputations, and ultimately profits of their respective companies. However, it is surprisingly common to overlook cybersecurity in industrial environments. Often, design departments focused on product development, or integrators focused on applications, unintentionally overlook all the necessary security considerations when it comes to edge or IoT solutions.
Every year, the technology industry introduces new or updated solutions, including increased connectivity. The trend towards connected devices aims to improve data collection and automation, which we fully support. However, cybersecurity must be a priority from the beginning, right from the initial design requirements document. During this phase, parameters are established that influence the selection of components for the final product (If you want to read more about specifications, read our blog Selecting the Right SBC for Edge Applications: A Decision-Making Guide ). For example, although they may seem harmless, decisions such as the number of USB ports can unintentionally create vulnerabilities. Choosing a platform with only essential USB ports minimizes this risk. On the software/firmware side, the system BIOS and boot process should also be carefully considered and documented.
Some may argue that custom hardware solutions are financially impractical for lower-volume deployments. In such cases, suppliers can offer their expertise to offer “customizations” of standard products. For example, Contec’s BX-M2500 box computer (visit our E-shop page) provides the capability to configure USB ports by selecting from several configuration options (see Figure 1). This feature, combined with BIOS password protection can greatly improve security.
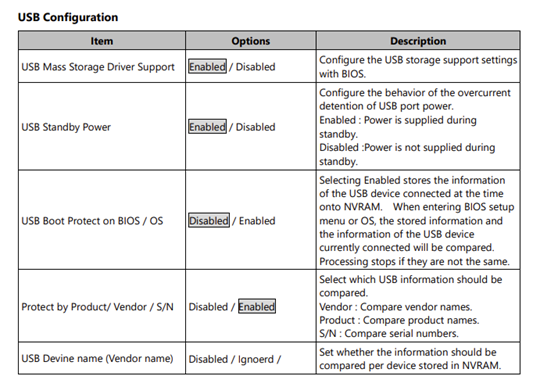
Figure 1. Extract from the Reference Manual of the BX-M2500 Series.
This example highlights how cybersecurity considerations shape hardware selection. Other important factors include the physical location of the device. Placing a boxed computer on a manufacturing line, can put it at risk of tampering, and potentially compromising data integrity. The end goal of cybersecurity is to protect that data, which comes in many different forms in industrial environments. For example, it is imperative to ensure that sensors properly communicate with the computers and that algorithms perform as expected, thus achieving the goal of protecting the data that enables the algorithm to function properly resulting in expected actions and outcomes.
The importance of a secure chassis in a solution is sometimes overlooked. This component provides not only protection from an often-rugged environment but also protection from cybercriminals. For example, now that we are in the age of artificial intelligence, the demand for advanced computing power is increasing daily. One of the platforms that excel in this application is Nvidia’s Jetson, which includes small, power-efficient modules and developer kits that power generative AI at the edge. However, relying solely on the SDK or module as a final solution is not enough; additional features are needed to ensure reliability. Part of that reliability lies in the chassis which serves as the first layer of security, providing a physical barrier, often including intrusion detection, that prevents easy physical access to the module and can alert security if the hardware is compromised. Contec box computers also include a variety of features that make them a more robust solution such as a wide range of input voltages, tolerance to high temperatures and dusty environments, standard certifications, and more. When considering cybersecurity requirements, it is essential to consider the consequences of physical access to a device. Choosing the right hardware is the first step to a secure system. (See Nvidia Jetson on our E-shop)
Finally, there are other features of security that you should look for, such as Trusted Platform Module (TPM), Hardware Security Module (HSM), and UEFI Secure Boot which improves security by strengthening the operating system (learn more in our blog Security at the Edge from a Hardware Perspective). By prioritizing cybersecurity in hardware selection, businesses can reduce the risk and the costs of lost data and damaged reputations. Read our blog "5 Tips on How to Apply Hardware Hardening to Your Facilities" for more information on minimizing risk at your facility.
In an increasingly connected and automated world, protecting data and systems is an ongoing challenge. However, investing more time and resources in designing a secure solution, with consideration for cybersecurity, will significantly reduce the risk of a cyber-attack giving you and your customers peace of mind.
